ALERT: YOU ARE BEING WATCHED!
Almost every day, we go online so we can keep in touch with the world and based on our interests, we either watch news, stock market, or spend time on social media and look at what is new and who is doing what? What is happening around us, what is the latest & the greatest, what are the new inventions, ideas and trends? Professionals go online to stay updated on the professional front.
Sharing posts about where we are and what we are doing keeps our near and dear ones excited and updated. Of course, it keeps us motivated.
Reports indicate that just few years ago, almost 80% smart phone users were using phones with location services enabled, the trend has now changed in the western world but in developing countries, still a very large number of users are not aware about the location services and privacy. Those in the IT world have known for a long time that every time we go online, we are leaving our digital footprint out there.
Some of us also think what all is secure and what is not so secure? When people innocently share their kid’s birthday photos, school graduation pics with other details, they do so thinking there is nothing to worry about! They think who is looking at these details?
But, little they know while staying online is a need but then staying secure while online is also a need. It is like driving on the road, while there is a need to be on the road to travel from one place to another but there is also a need to take all precautions to stay safe on the road.
Let us talk about Cyber Security – this is something that needs attention of everyone because in today’s day and age, Cyber Security must fall into everyone’s “need to understand and comply” scope.
Today all across the world, businesses have their presence online – directly or indirectly. Majority of business have some presence online When all our clients are online, where else would we promote our business? So, many of the marketing campaigns are happening online.
All these businesses also need to understand, and follow cyber security norms and stay safe. What all are we sharing online in our marketing campaign? For example, If we are sharing our IT/Network structure, hackers will know how to crack it.
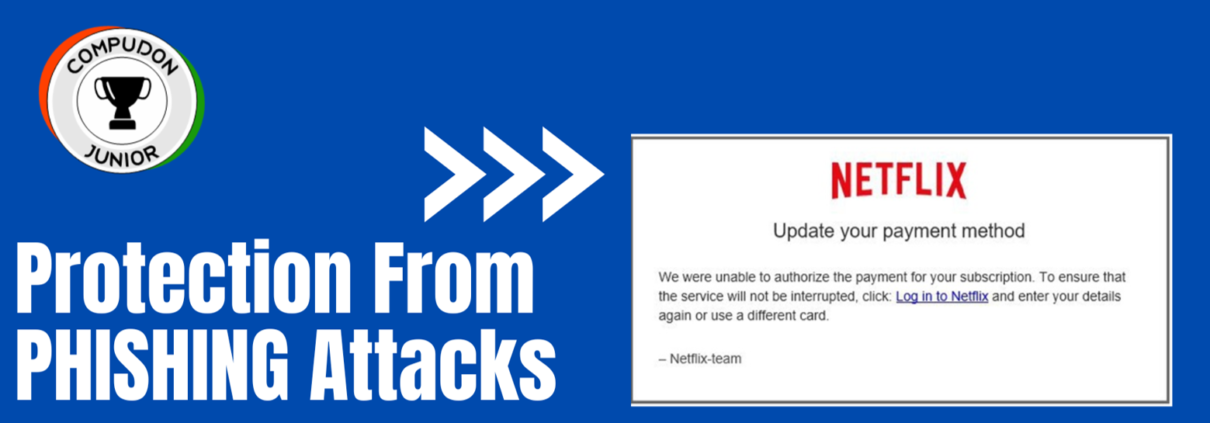
Simply put, all the information put out online is “publicly available information”. In the world of cyber security, this is called open source intelligence (OSINT). Here, open source means that the sources that provide information are open/public. OSINT is an important part of Recon (Reconnaissance).
Different stages in Cyber Security are,
- Pre Security
- Offensive Pen testing
- Cyber Defense
For Cyber Security professionals, working at any of the above stages, Recon is the very first step taken whenever they get ready to perform Vulnerability Assessment or Penetration Testing. While Active Recon includes direct interaction with the target, Passive Recon includes finding and using the information available on the web.
For Passive Recon, there are some very powerful tools available that will check the target’s online presence, from various different domains, social media platforms, what all has been shared, when it was shared, patterns are set and noted, Pictures and Videos are retrieved and these tools help Cyber Security professionals put very important, and sometimes, private and sensitive information together. These professionals are then able to join the dots and infer the underlying secrets/information.
OSINT or Recon tools are not magical. They only pull out publicly available information and put it together for these professionals to join the dots. Many a times, to start the Recon, all the professionals have with them is a name, or if they are lucky, an email address, or a domain. They start digging with it and in very little time they have a great amount of intel with them.
Once they know something like a website they can use, they will try and find out weaknesses, if any, that they can exploit. This is the process of Vulnerability Assessment. A part of the website might be weak/vulnerable or using some outdated technology, and becomes vulnerable.
Once a vulnerability is found, the next process of Penetration testing begins. Here, those vulnerabilities are targeted and exploited. The experts try and get into the target’s network, system, database, based on the type of vulnerability. Once they are in, they will try and exploit it, causing damage to the target’s assets. Many a times, cookies from a device give away access to sensitive data.
To stay safe, it is important to clear your browsing history from time to time. Delete all cookies from your device from time to time. When you are using your browser to look at confidential, private or sensitive information, it is not a bad idea to use Incognito mode. Today we have the options available for using encrypted emails.
Firewalls will protect you when you are approached from an unknown website. Antivirus software are available for your further protection and there are range of protective software available. These are the most common, easily available and easy to implement security measures that we should follow.
As a common practice, companies pay the ethical hackers to find vulnerabilities in their system and some companies even pay them to penetrate into the company’s internal assets and see what kind of exploitations are they vulnerable to. If hacker is able to find vulnerabilities on the target’s request, the proof is shared with the target to enhance the security and eliminate the vulnerabilities.
To summarize, we agree that staying online is a need and that staying secure while online is a need too. Cyber Security, I think, should have a place in everybody’s “need to understand and comply” scope.
Stay Online, Stay Safe!
Author: Shital Rai
LinkedIn: www.linkedin.com/in/shitalrai